
March 1, 2023
This week we're taking you behind the scenes of your cloud environment and looking at vSphere virtual networking, including the difference between virtual switches/networks and their physical counterparts, plus the primary configuration options for vSwitches and vLANs.
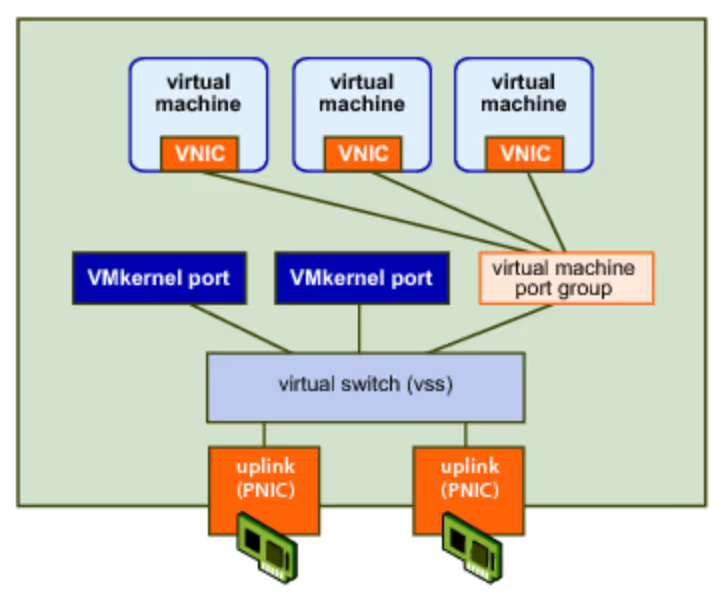
Similar to the general concept of virtual machines, virtual network switches aren’t really much different from their physical counterparts. Incoming traffic follows regular TCP/IP network protocol and traverses the same layers, so practical management remains the same. That means the servers running your virtual machines can use regular network adaptors from pretty much any vendor. Unlike physical network components, vSwitches allow on-the-fly configuration changes without ever touching your server hardware.
At the Layer 2 level (OSI Data-Link layer model), vSwitches only pass network traffic to MAC addresses that are assigned to connected devices. In other words, if a virtual machine or port device is not actively using a virtual port on the vSwitch, the switch does not know it exists. With a physical switch, a large table of MAC addresses is stored in memory, and unknown incoming traffic is sent to all of them in order to learn where to send that traffic in the future.
“But wait”, I hear you saying. “What if one of my VMs sends an unknown MAC address through my virtual switch? Won’t it just ignore that traffic?”
vSwitches only ignore incoming network frames when they are coming from an external source. Internal source traffic gets passed on to a physical uplink. External VLANs, like a separate virtual machine cluster or network segment, use Layer 3 switching. Therefore if the MAC address is assigned to another VLAN, the physical uplink is also engaged.
These physical uplinks, or NIC network adapters, pass data into and out of the virtual data center. Your virtual machine host servers will have NICs installed. If you aren’t using your virtual servers to communicate outside of themselves, whether with external networks or the larger internet, you don’t need a NIC. Otherwise, you can use a single NIC or even a couple dozen, allowing many Ethernet ports.
vSwitches can scale their ports to the currently provisions VMs and hosts, keeping memory consumption down and adding them when necessary. These elastic ports are automatically managed by vSphere.
Each virtual network adapter attached to a VM uses a virtual port. Virtual ports act as a bridge between the vSwitch and the NIC. There are also specific types of ports called VMkernel ports. These allow the actual host platform to connect to vCenter and other hosts on the network. Functions include vCenter and vSphere management, vMotion, fault tolerance, and storage traffic (iSCSI or NFS).
Virtual LANs help control the network traffic being forwarded by switches. VLANs allow segments of the network to only send traffic to each other by default. Normally, a host would receive and respond to every incoming request, which can cause a cascading effect across the entire network. To send traffic between VLANs, as mentioned above, a Layer 3 device such as a router must be engaged, unless you have a network switch capable of routing.
In vSphere, there are three types of VLANs.
External Switch Tagging (EST) VLANs keep the physical uplink in charge of VLAN network tags. Network traffic destined for different VLANs are passed through an external physical switch rather than the vSwitch. The physical ports on the switch have Access mode activated under EST, which strips the VLAN tag before passing on the traffic. Because of this, EST is best suited to single VLAN configurations. All traffic on the vSwitch must use the same VLAN, which is configured to the access port on the physical switch.
Virtual Switch Tagging (VST) has the vSwitch inspect, add, or remove VLAN tags. The upstream port is set as a trunk port rather an access port, allowing a predefined number of VLAN traffic through to the vSwitch. The vSwitch checks the VLAN tag and the MAC address to determine the end destination. If it recognizes the VLAN tag, it removes the tag before passing on the traffic. If it doesn’t know the VLAN tag, the traffic is dropped. Going the other direction, like from a NIC or VMkernel port, causes the vSwitch to add a VLAN tag before passing it on to the physical uplin
Virtual Guest Tagging (VGT) keeps the trunk configuration on the upstream physical switch, so VLAN tags make it through to the vSwitch. The vSwitch, however, does not strip the tag before passing it on. The virtual machine must be configured to read VLAN tags and add them to outgoing traffic as well. This can be manually set under Ethernet Adapter settings in the Operating System of a VM. Use cases for VGT include VMs that must monitor or route network traffic.
